Configuration
ldapsearch -Y EXTERNAL -H ldapi:/// -b cn=configOutput
...
olcDatabase: {-1}frontend
olcAccess: {0}to * by dn.exact=gidNumber=0+uidNumber=0,cn=peercred,cn=external
,cn=auth manage by * break
olcAccess: {1}to dn.exact="" by * read
olcAccess: {2}to dn.base="cn=Subschema" by * read
olcSizeLimit: 500
# {0}config, config
dn: olcDatabase={0}config,cn=config
objectClass: olcDatabaseConfig
olcDatabase: {0}config
olcAccess: {0}to * by dn.exact=gidNumber=0+uidNumber=0,cn=peercred,cn=external
,cn=auth manage by * break
olcRootDN: cn=admin,cn=config
# {1}mdb, config
dn: olcDatabase={1}mdb,cn=config
objectClass: olcDatabaseConfig
objectClass: olcMdbConfig
olcDatabase: {1}mdb
olcDbDirectory: /var/lib/ldap
olcSuffix: dc=betrayer,dc=com
olcAccess: {0}to attrs=userPassword by self write by anonymous auth by * none
olcAccess: {1}to attrs=shadowLastChange by self write by * read
olcAccess: {2}to * by * read
olcLastMod: TRUE
olcRootDN: cn=admin,dc=betrayer,dc=com
olcRootPW: {SSHA}hSq1jYDjHfdS/Gi+uxLV1cFM/hOtMT1E
olcDbCheckpoint: 512 30
olcDbIndex: objectClass eq
olcDbIndex: cn,uid eq
olcDbIndex: uidNumber,gidNumber eq
olcDbIndex: member,memberUid eq
olcDbMaxSize: 1073741824
# search result
search: 2
result: 0 Success
# numResponses: 11
# numEntries: 10As said in the Task we find the important Information at the End of the Output.
To Change these Settings we need to define and LDIF File with the required properties.
In our Case we call the file add_olcRootPW.ldif.
It should look like this
# add_olcRootPW.ldif
dn: olcDatabase={0}config,cn=config
replace: olcRootPW
olcRootPW: {ssha}U1oLsngiAsXhFQrav5UzHxn2/9qPNcL+Then we can modify ldap with the ldapmodify command and our new ldif file.
ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f ~/add_olcRootPW.ldifOutput
modifying entry "olcDatabase={0}config,cn=config"Connect to Config
Now we can connect to our LDAP Config in Apache Directory Studio. The Connection Process should look like this.
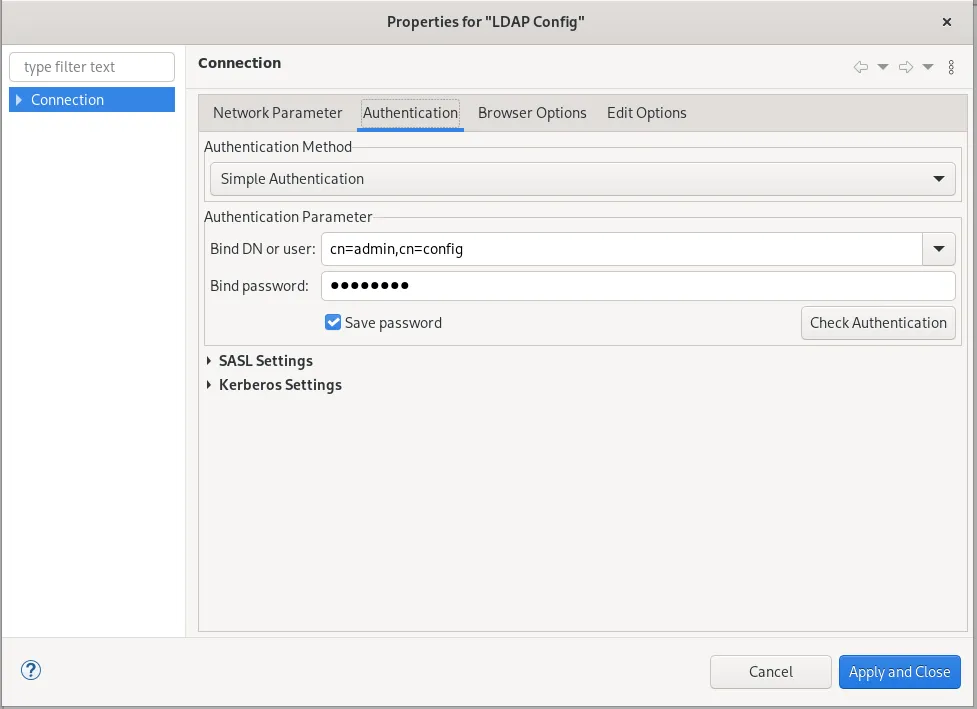
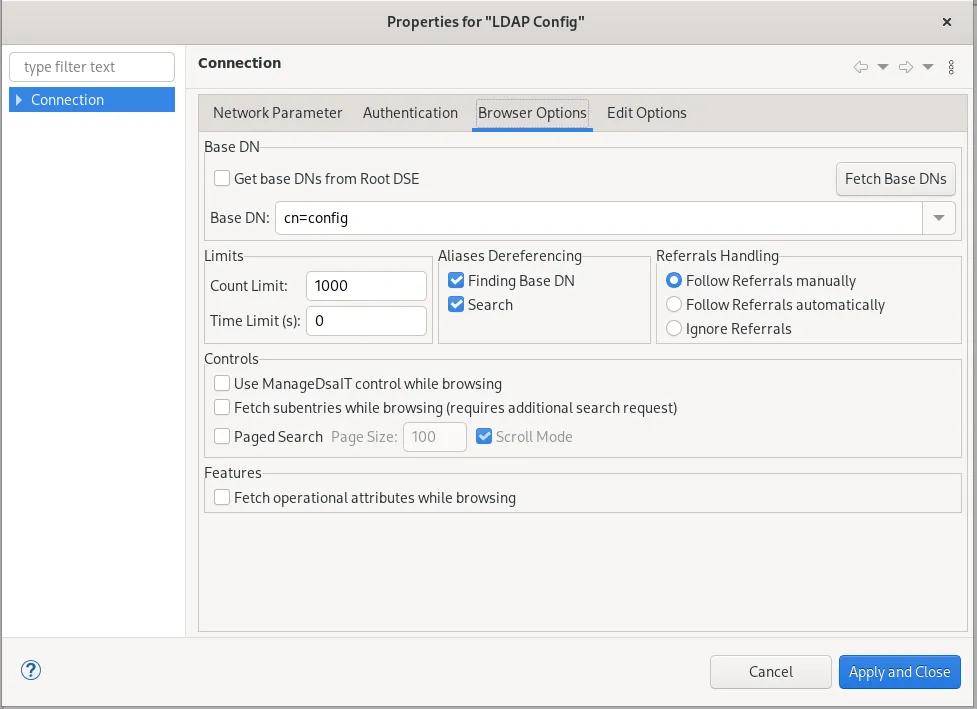
After we are connected we can set the olcLogLevel to -1 to get the most Information in our logs.
To see the logs we can open the file /var/log/syslog
We can now see that our ldap server is creating logs.
Aug 1 09:32:21 sdi01a slapd[46520]: => access_allowed: read access to "cn=config" "olcArgsFile" requested
Aug 1 09:32:21 sdi01a slapd[46520]: <= root access granted
Aug 1 09:32:21 sdi01a slapd[46520]: => access_allowed: read access granted by manage(=mwrscxd)
Aug 1 09:32:21 sdi01a slapd[46520]: => access_allowed: result not in cache (olcPidFile)
Aug 1 09:32:21 sdi01a slapd[46520]: => access_allowed: read access to "cn=config" "olcPidFile" requested
Aug 1 09:32:21 sdi01a slapd[46520]: <= root access granted
Aug 1 09:32:21 sdi01a slapd[46520]: => access_allowed: read access granted by manage(=mwrscxd)
Aug 1 09:32:21 sdi01a slapd[46520]: => access_allowed: result not in cache (olcToolThreads)
Aug 1 09:32:21 sdi01a slapd[46520]: => access_allowed: read access to "cn=config" "olcToolThreads" requested
Aug 1 09:32:21 sdi01a slapd[46520]: <= root access granted
Aug 1 09:32:21 sdi01a slapd[46520]: => access_allowed: read access granted by manage(=mwrscxd)
Aug 1 09:32:21 sdi01a slapd[46520]: => access_allowed: result not in cache (olcLogLevel)
Aug 1 09:32:21 sdi01a slapd[46520]: => access_allowed: read access to "cn=config" "olcLogLevel" requested
Aug 1 09:32:21 sdi01a slapd[46520]: <= root access granted